Phishing attacks are rapidly increasing against Microsoft 365 tenants. Why? Microsoft is used by many company’s and users, so targetting it is very attractive. Also, techniques to bypass Multi-Factor Authentication (MFA) during a phishing attack are gaining popularity (AiTM phishing attacks). This allows attackers to even compromise accounts protected by MFA.
At Zolder we are securing many Microsoft tenants for our customers using our Attic app. Also, we are regularly investigating phishing attacks. We also created didsomeoneclone.me – a (free to use) solution to detect and mitigate malicious clones of your website.
This led us to the question: is it possible to detect (AiTM) phishing attacks on a Microsoft tenants Login page?
Introduction to AiTM attacks
AiTM stands for adversary in the middle. In a AiTM attack the victim connects to a server controlled by the attacker. The attacker forwards the requests of the victim to the final destination. In this case the real Microsoft tenants login portal (login.microsoftonline.com). Any responses from the Microsoft login portal are redirected back to the victim. The attacker is acting as a man-in-the-middle.
During the attack the attacker is able to sniff the users login credentials, or the session cookies. In the worst case this leads to full take over the phished account.
A commonly used tool to perform AiTM attacks is Evilginx. Also, cybercriminals are offering custom AiTM-platforms, such as STORM-1575.
How to detect AiTM phishing attacks on my Microsoft tenant?
During our work we found out that Microsoft offers features to customize the branding of your Microsoft tenants login page. Here is an example of a default login page:
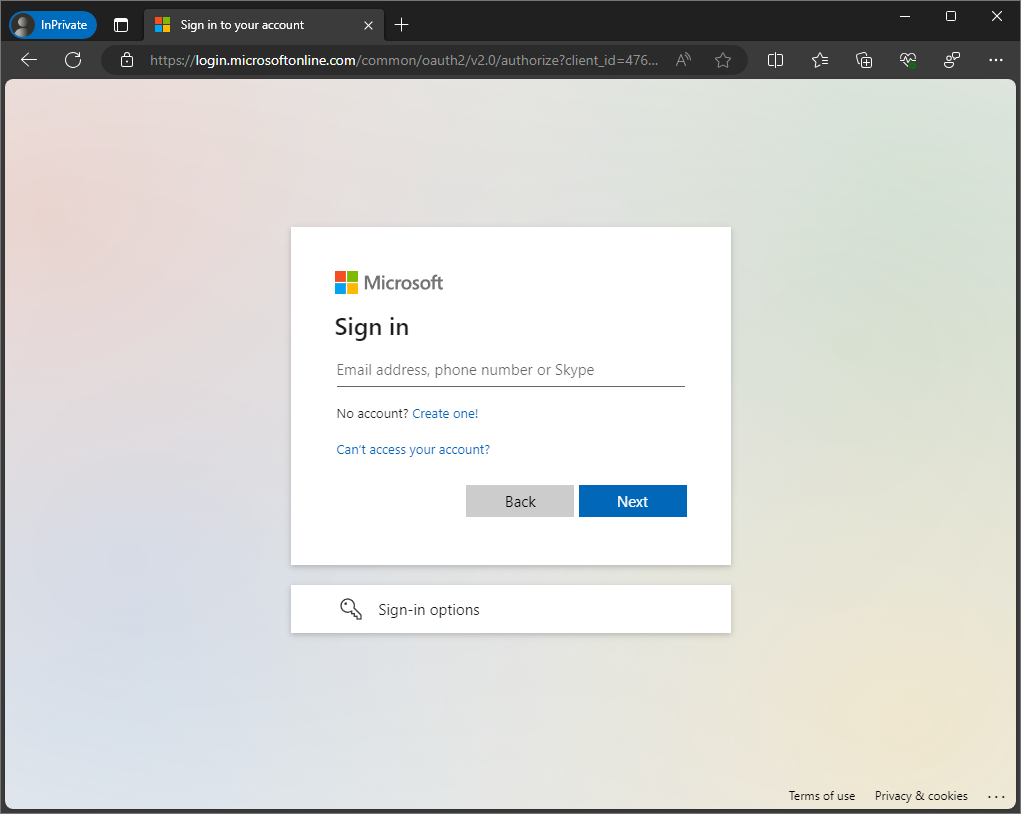
One of the features is customizing the CSS of the page. This made us curious: could we leverage the implementation of didsomeoneclone.me to detect phishing attacks on this page?
The tool didsomeoneclone.me requires users to embed a script into their website in order to work. The embed forces the browsers of visitors to make a request to the backend of didsomeoneclone.me. The backend analyses the incoming request, and checks whether it is originated from the original website or a phishing website. If the request originates from a phishing website, the website owner is notified. A pretty simple but effective concept.
If we could make the browsers of the Microsoft page visitors connect to the didsomeoneclone.me backend, this should work aswell.
Creating the CSS file
We started playing around with the CSS feature. We ended up with the following simple CSS file:
.ext-footer
{
background-image: url('https://dscm.li/test');
background-size: 0 0;
}This CSS file attempts to load a background-image hosted at the didsomeoneclone.me backend. The background-size makes the image invisible. Now it’s time to validate whether our idea works!

Using the browser inspect, we validated that a request to the didsomeoneclone.me backend is indeed made. Cool! But does it also work when using the AiTM tool Evilginx? Let’s validate! We spinned our own Evilginx infrastructure on the domain aitm.tech. After visiting the page and logging in with our own account, we validated that the image was indeed loaded:

Also the didsomeoneclone.me backend detected the clone successfully:
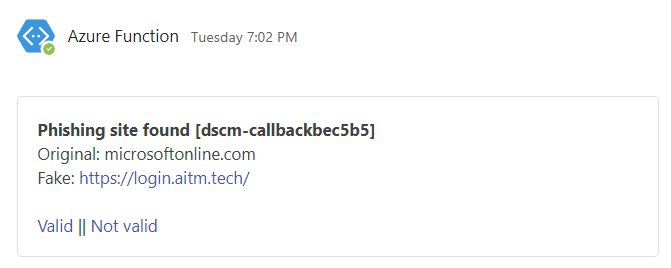
💥Cool! This allows us to detected phishing attacks on our Microsoft login page. Even AiTM phishing attacks are covered (at least in the case of Evilginx).
Implementing the techniques into our products to protect our customers
We proved that the technique works. We don’t want to just prove this, but we also want to have an impact by protecting our customers with the idea.
didsomeoneclone.me
We developed a manual on how to implement this new technique in your Microsoft tenant manually. With a few steps, you are able to protect your Microsoft tenant. The tool will sent a email notification whenever someone uses your Microsoft login page in a phishing attack. This detection can be installed at no costs using the free plan.
Attic app
Using our Attic app we are already securing many Microsoft tenants. This allows us to further integrate the technique because we do already have access to Microsoft tenants. This has multiple advantages:
- Our already onboarded customers are able to install the CSS with a single click – no technical knowledge is required
- 24/7 Monitoring to check if the technique is still installed (correctly)
- Notifications are sent via mobile app push notifications
- Communication with Zolder experts is possible whenever a detection occurs
- Execute a remedation
Currently the language of our app is mainly Dutch. We will make it multi language soon. Therefor, if you’re not Dutch and you’d like to implement this, we would recommend using didsomeoneclone.me directly. Otherwise if you are Dutch we recommend to use the Attic app.
Conclusion
Using this technique we are able to detect phishing attacks against our Microsoft tenant. It’s very simple, and very effective with a low false positive rate. Of course, we will never catch 100% of the attacks and this can be bypassed. But, we believe that it’s better then nothing at all.
Thanks for reading!
