Business Email Compromise (BEC) fraud is a collection of fraud techniques revolving around the modification of payment information or spoofing of invoices. According to the FBI in 2019 cybercrime related damages cost companies 3,5 billion dollars, BEC fraud was responsible for 50% of that resulting in 1,7 billion dollars in damages! Assuming that the FBI only records this for US based companies the actual damages worldwide are likely more than double.
Access to the email account is usually gained via phishing, brute force attacks or bought on specific marketplaces. Depending on the approach of the attack, the initial vector can be hard to detect. If the attackers buys access to a user account, the only thing you’d see is a logon. (assuming there’s no MFA). Stores like Genesis sell credentials, you can even search for specific domains in order to find targets.
Detecting the attacks can be difficult. While looking for more information into the subject I came across a couple of insightful blogs. But most where there just to warn users of a nameless threat without supplying any information that could help the reader protect his or her organization. A recent blog from Checkpoint shows a more practical insight into an attack from a group they dubbed: “Florentine Banker”. Looking at the attack we can see the attackers moving specific emails to a separate folders. Checking other blogs describing these attacks show similar behavior.
There are a couple of places where we could focus to detect the attacks.
- Phishing/brute forcing/buying of credentials
- Initial login
- Modification of email box (often via rules)
- Sending of fake invoices
Azure Sentinel & O365
For the purpose of this blog we will look at the creation of email rules and specifically ones that seem BEC fraud related. We can try to detect some of this behavior using Azure Sentinel and o365. We can modify some of the rules we built in an earlier blog to detect email rule abuse.
Before we can start building the rules we need to know what the rules look like. Based on the publicly available information some actors also mark messages as read in order to hide their actions. We use the following characteristics to build our rules:
Folders used:
- Archive
- RSS Subscription
- Junk Email
- Conversation History
Keyword list (Dutch focused):
- factuur
- betaling
- aanmaning
- invoice
- overboeking
- payment
operations:
- Move emails from specified sender to folder
- If the subject or body contains keyword forward to certain email
- If the subject or body contains move to folder
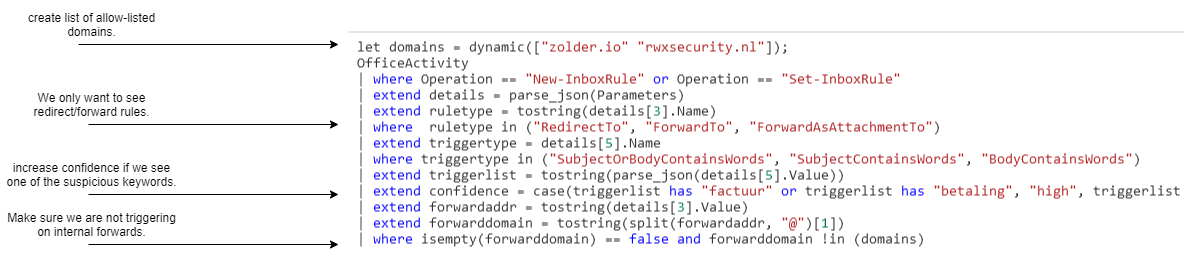
We created four different rules and uploaded them to our o365 Github repository. If you use Azure Sentinel make sure to use the rules to monitor for suspicious behavior. There are four rules related to BEC fraud in our public repository:
- from sender move to folder
- subject or body contains a keyword move to folder
- two rules related to forwarding and redirecting.
Our regular Outlook mail rules will trigger at the same time that the BEC fraud related ones trigger. The first are generic, the second are more specific and help you triage what might be happening.
Blogs used as a source for the rules we created: